Top 5 Security Mistakes Companies Make Before Hiring an MSP

How Security Gaps Form Before MSP Engagement
Security challenges often develop during periods of growth, limited budgets or non-technical oversight. As environments expand, security policies, credential management and monitoring practices struggle to keep pace. These conditions create blind spots that weaken the organization’s security posture and are frequently uncovered during MSP discovery and assessment.
The Top 5 Security Mistakes
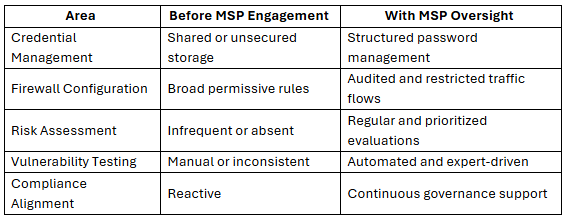
1. Storing Credentials in Shared or Unsecured Locations Increases Access Risk
Sensitive credentials stored in shared folders, documents or unsecured files expose critical infrastructure to internal and external risk. Passwords for network devices, firewalls and servers require controlled access and structured management to reduce compromise exposure.
2. Leaving Default Credentials Active on Critical Systems
Infrastructure components such as UPS systems, network devices and administrative platforms often ship with default credentials. Leaving these unchanged allows unauthorized access that can disrupt power, availability and system continuity.
3. Allowing Overly Permissive Firewall Rules Exposes Companies to Risk
Firewall rules that allow unrestricted traffic effectively remove perimeter protection. Rules designed to resolve temporary functionality issues frequently remain in place, exposing the environment to unnecessary risk. Security posture improves when traffic flows are reviewed, documented and restricted to required connections.
4. Skipping Regular Risk Assessments and Vulnerability Testing
Risk assessments identify weaknesses across hardware, device security and software configurations. Vulnerability testing uncovers misconfigurations, unpatched flaws and outdated systems. Without these evaluations, organizations struggle to prioritize threats or respond efficiently to commonly exploited attack vectors.
5. Treating Compliance as a One-Time Requirement
Regulatory compliance requires continuous alignment, monitoring and validation. Industries governed by HIPAA, PCI DSS and GDPR face increasing complexity as environments evolve. Failure to understand applicable requirements early introduces operational disruption and financial exposure later.
Key Benefits of Addressing These Mistakes Early
Stronger Security Foundations
Proactive identification of credential risks, firewall exposure and configuration gaps creates a resilient security baseline that supports a stable security posture before MSP onboarding.
Reduced Risk Exposure
Early remediation minimizes attack surfaces and limits the likelihood of breach escalation or service interruption.
Improved MSP Onboarding Efficiency
Clean security baselines allow MSPs to implement monitoring, governance and protection frameworks faster and more effectively.
Regulatory Confidence
Clear compliance alignment strengthens trust with customers, partners and stakeholders.
Security Before and After MSP Engagement
How to Prepare for MSP Security Partnership
Organizations benefit most when preparation begins before formal engagement and focuses on strengthening baseline security posture.
- Review where credentials are stored and how access is controlled
- Identify systems using default or shared credentials
- Document firewall rules and confirm business justification
- Schedule initial risk assessments and vulnerability testing
- Map applicable compliance requirements to current practices
These steps accelerate MSP discovery and strengthen long-term security outcomes.
Key Takeaways
- Credential management gaps expose infrastructure to unnecessary risk
- Default system credentials weaken availability and control
- Overly permissive firewall rules undermine perimeter security
- Regular risk assessments and testing strengthen threat readiness
- Continuous compliance alignment supports trust and resilience
FAQ
Why do MSPs focus on proactive threat identification?
Proactive monitoring and detection allow risks to be identified and contained before escalation, reducing operational disruption and exposure.
What security foundations should exist before MSP onboarding?
Organizations benefit from establishing baseline security controls before onboarding an MSP. These foundations include secure credential management, removal of default system passwords, documented firewall rules, initial risk assessments, vulnerability testing and a clear understanding of applicable compliance requirements. Establishing these elements early allows the MSP to focus on strengthening security posture, accelerating monitoring deployment and aligning protection with long-term business goals.
What is the difference between risk assessments and vulnerability testing?
Risk assessments evaluate overall exposure across infrastructure and operations, while vulnerability testing identifies specific weaknesses in configurations, software and systems.
Why does compliance matter beyond regulations?
Compliance fosters trust with customers and partners by demonstrating responsible data handling and security maturity.
When should compliance planning begin in the MSP process?
Compliance planning should begin before engagement to ensure governance alignment during onboarding and ongoing operations.



%20(1).png)


.jpg)


